網路機房維護 #1213
進行中防火牆安全漏洞 - Multiple Fortinet Products' FortiCloud SSO Login Authentication Bypass
概述
Summary
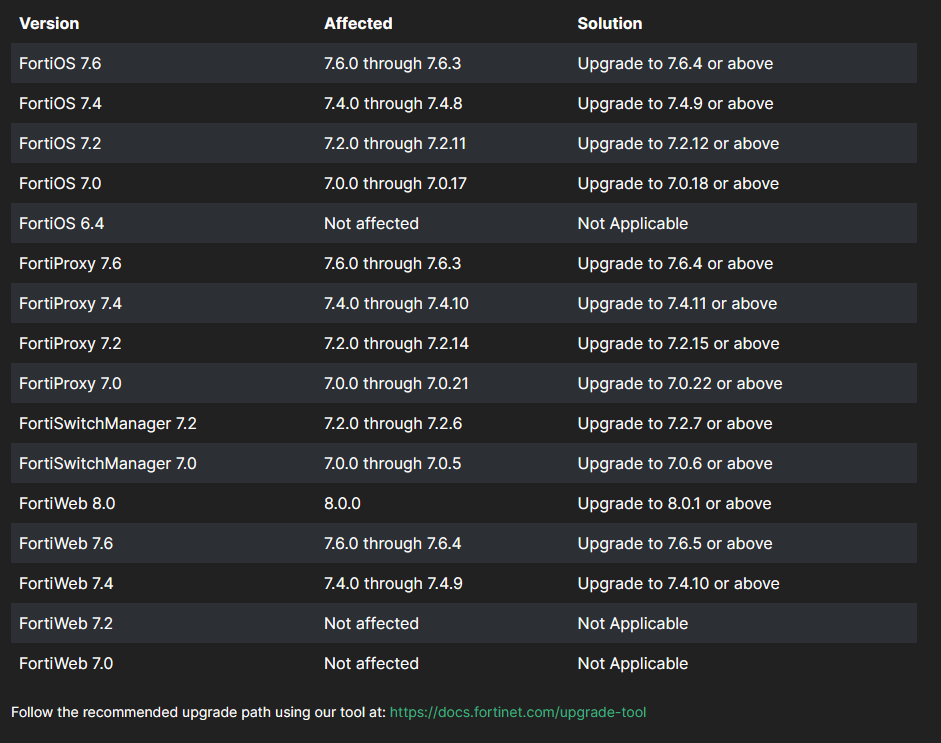
An Improper Verification of Cryptographic Signature vulnerability
[CWE-347] in FortiOS, FortiWeb, FortiProxy and FortiSwitchManager may
allow an unauthenticated attacker to bypass the FortiCloud SSO login
authentication via a crafted SAML message, if that feature is enabled on the device.
Please note that the FortiCloud SSO login feature is not enabled in default factory settings. However, when an administrator registers the device to FortiCare from the device's GUI, unless the administrator disables the toggle switch "Allow administrative login using FortiCloud SSO" in the registration page, FortiCloud SSO login is enabled upon registration.
To prevent being affected by this vulnerability on vulnerable
versions, please turn off the FortiCloud login feature (if enabled) temporarily until
upgrading to a non-affected version.
To turn off FortiCloud login, go to System -> Settings -> Switch
"Allow administrative login using FortiCloud SSO" to Off. Or type the
following command in the CLI:
config system global
set admin-forticloud-sso-login disable
end
檔案
