專案資訊 #1066
進行中專案資訊 #1064: 2025-PenTest
Domain Admin Vulnerable to Kerberoasting Attack
100%
概述
NN "4.3.2
MITRE-T1558
" "Domain Admin Vulnerable to Kerberoasting Attack
It is possible to obtain the encrypted Kerberos service ticket of a domain admin for offline password cracking.
" "The exposure of encrypted service ticket empowers adversary to reveal the exact password to perform user impersonation or privilege escalation in this case.
It is noteworthy that the affected domain admin has never expiring password and has its password remain unchanged more than 2 years. This allows adversary ample time to perform offline cracking of its password.
" "Avoid assigning SPNs to Domain Admin accounts unless absolutely necessary.
Set long and complex passwords for service accounts and limit privileges of service accounts. If possible, use AES encryption instead of RC4 encryption."
檔案
是由 益利 周 於 約 2 個月 前更新
- 檔案 clipboard-202511271337-vwsq1.png clipboard-202511271337-vwsq1.png 已新增
- 檔案 clipboard-202511271343-ve3dx.png clipboard-202511271343-ve3dx.png 已新增
- 狀態 從 New-新增 變更為 Resolved-解决
- 完成百分比 從 0 變更為 100
1.新增 一般使用者 Domain User 授予 SPN
2.移除 Domain Admin 網域管理員帳戶的 SPN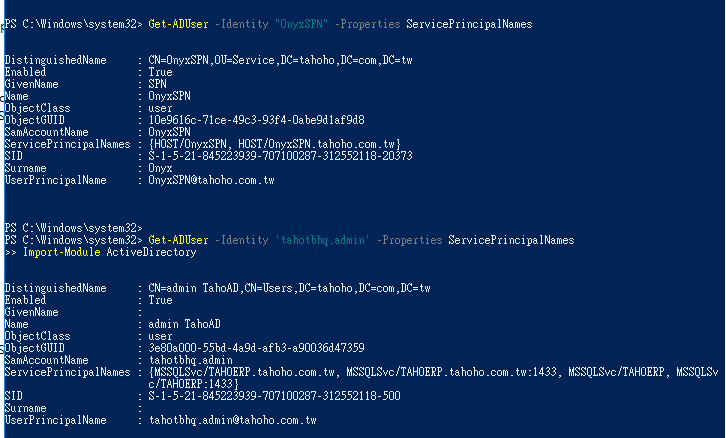
3.變更 網域管理員帳戶 密碼
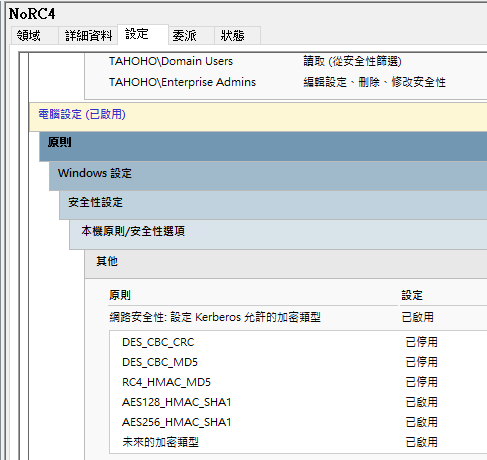
4.設定群組原則 限用 AES 加密,不使用 RC4 加密